Beyond the Hype: Practical Steps for OEMs to Achieve CRA Compliance
The EU Cyber Resilience Act isn't just another regulatory checkbox. For equipment OEMs, it represents a fundamental shift in how products are designed, developed, and maintained throughout their lifecycle. While awareness of the CRA is growing, many manufacturers struggle with a critical question: Where do we actually start?
The good news is that compliance doesn't have to be overwhelming. The German Federal Office for Information Security (BSI) has published Technical Guideline TR-03183-1, which provides a structured framework for achieving CRA readiness. This guide translates those requirements into five practical steps that equipment OEMs can implement systematically.
By December 11, 2027, when CRA enforcement begins, you need to have these processes in place. Let's break down exactly what that means in practice.
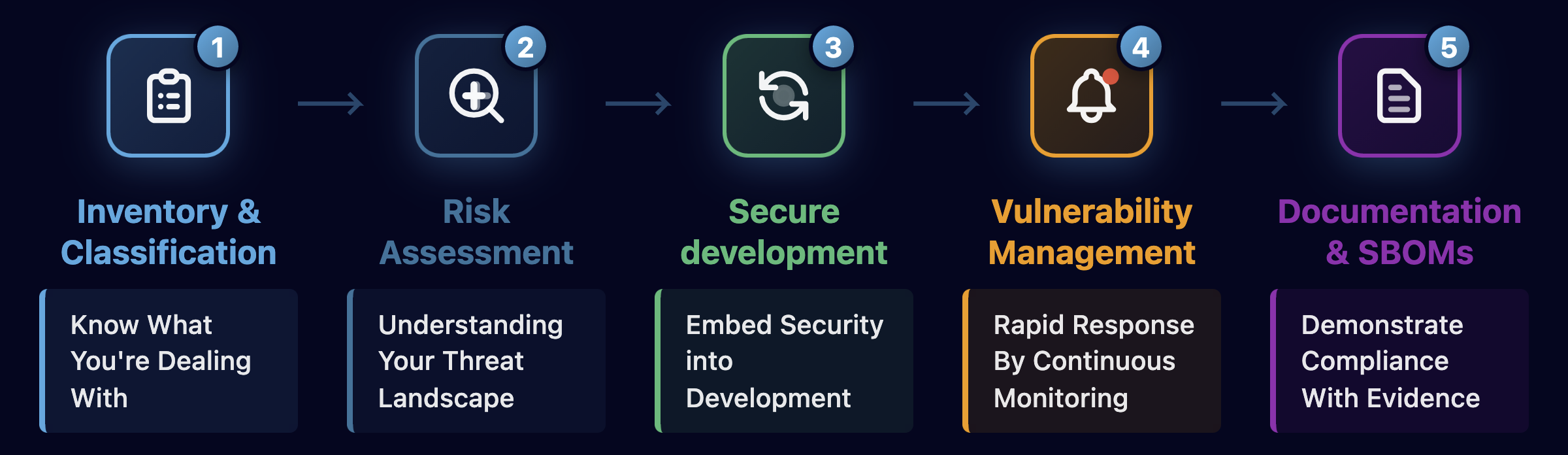
Step 1: Inventory & Classification
The Foundation: Know What You're Dealing With
You cannot secure what you don't know exists. The first step toward CRA compliance is conducting a comprehensive inventory of all products with digital elements in your portfolio and classifying them according to CRA requirements.
Identifying Digital Elements
Start by cataloging every product that contains:
- Software components (embedded firmware, operating systems, applications)
- Hardware with programmable elements (microcontrollers, FPGAs, PLCs)
- Network connectivity (wired, wireless, or intermittent)
- Data processing or storage capabilities
- Remote access or diagnostic features
Don't overlook products that only occasionally connect for updates or diagnostics. If it has digital elements and can communicate with other devices or networks, directly or indirectly, it falls under CRA jurisdiction.
Classification Under CRA
The CRA uses a risk-based tiered classification system that determines your conformity assessment requirements:
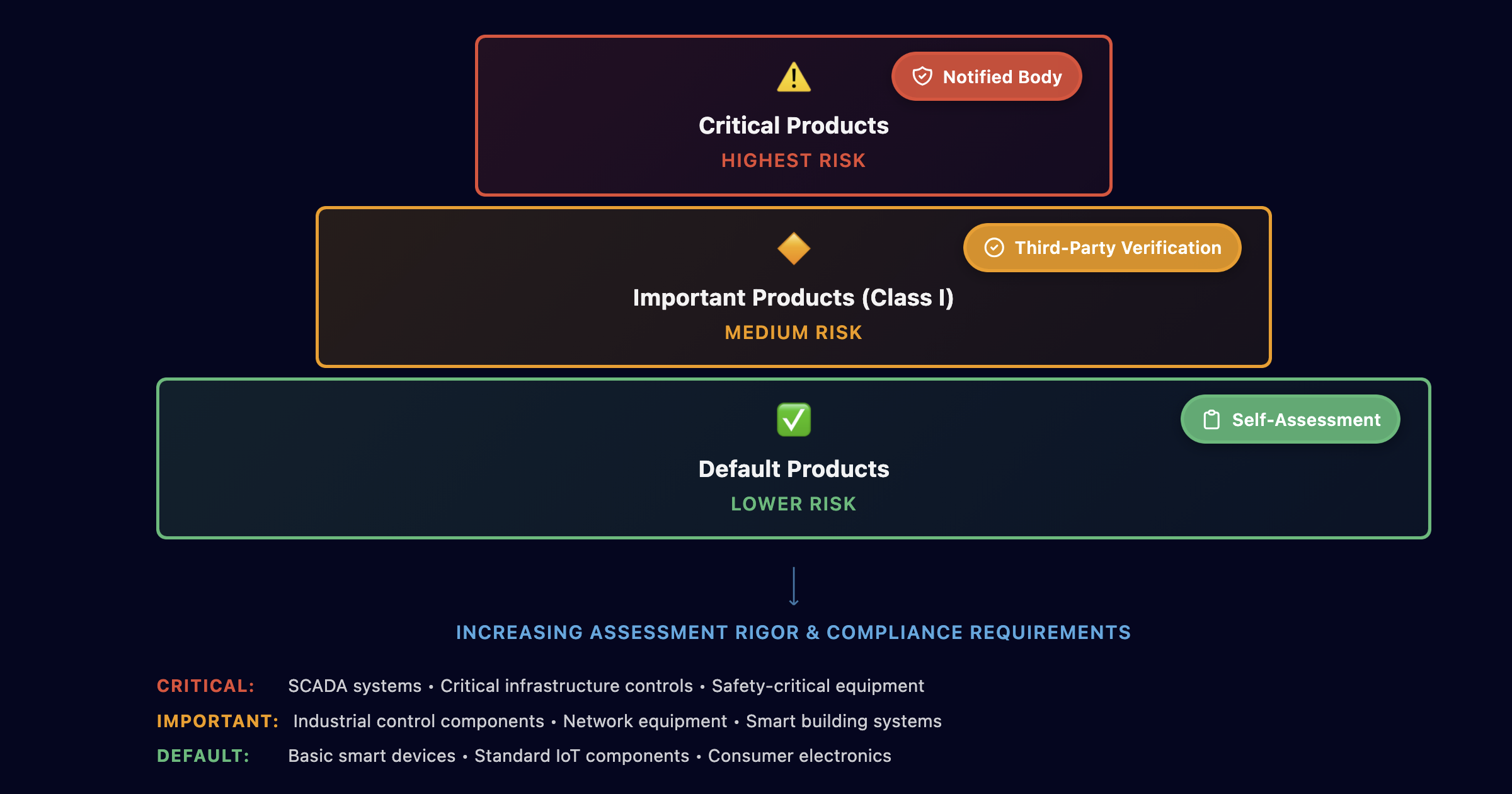
Default Products: Lower-risk products requiring manufacturer self-assessment. While less stringent, you still must meet all essential security requirements and maintain comprehensive documentation.
Important Products: Medium-risk products requiring assessment against established standards with third-party verification by notified bodies. Many industrial control components fall into this category.
Critical Products: Highest-risk products demanding mandatory assessment by notified bodies according to applicable standards. This includes industrial control systems, SCADA components, and safety-critical equipment.
Classification isn't arbitrary. Consider your product's:
- Intended use case and deployment context
- Potential impact if compromised
- Role in critical infrastructure
- Access to sensitive data or systems
Building Your Product Matrix
Create a detailed matrix documenting:
- Product names and model numbers
- Digital elements present in each product
- CRA classification (Default/Important/Critical)
- Current development status (in production, in development, legacy)
- Expected lifecycle duration
- Target markets and applicable regulations
This matrix becomes your roadmap, helping you prioritize efforts and allocate resources effectively. Products launching soon or classified as Critical demand immediate attention.
Step 2: Risk Assessment
Understanding Your Threat Landscape
The CRA mandates thorough cybersecurity risk assessments for each product. But this isn't a one-time exercise completed during initial design. As BSI TR-03183-1 emphasizes, risk assessment is a continuous process that must be updated throughout the product lifecycle.
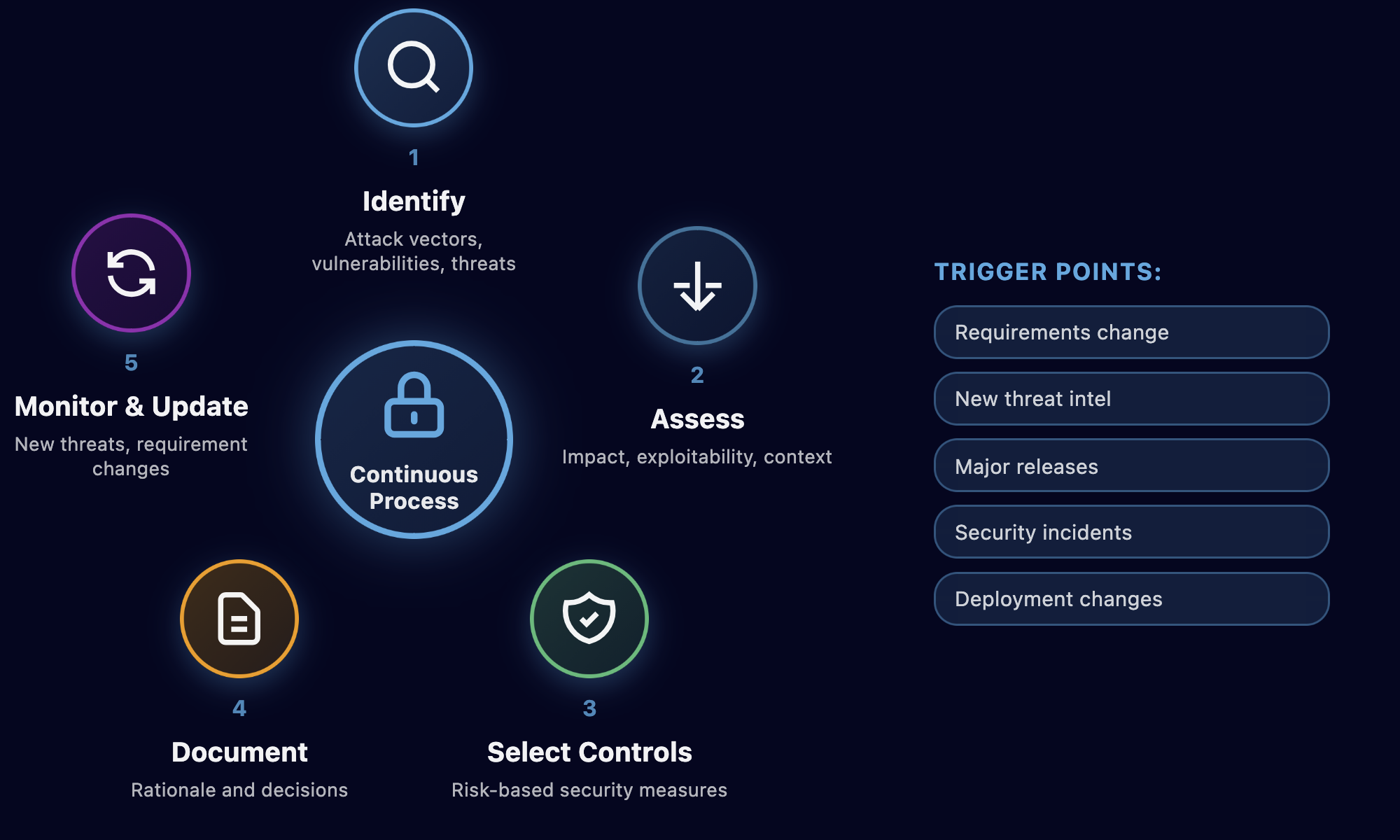
When to Conduct Risk Assessments
Contrary to common practice, risk assessment cannot wait until after development. You must conduct risk assessments during the earliest project phases, ideally during design and planning stages. This ensures security considerations drive architectural decisions rather than being retrofitted later.
Continue updating risk assessments:
- When requirements change
- When new threat intelligence emerges
- Before major releases or updates
- After security incidents or near-misses
- When deployment contexts change
What to Assess
Your risk assessment must identify:
Attack Vectors: How could adversaries gain access to your product? Consider physical access, network interfaces, supply chain vulnerabilities, and social engineering vectors.
Vulnerability Exploitation Scenarios: What weaknesses could attackers exploit? Evaluate both known vulnerability classes and product-specific weaknesses.
Context-Specific Threats: Vulnerabilities deemed exploitable for one device may not apply to another based on intended use. A control system in an air-gapped environment faces different threats than internet-connected equipment.
Business Impact: What are the consequences if security fails? Consider operational disruption, safety hazards, data breaches, and reputational damage.
Risk-Based Security Measures
BSI TR-03183-1 provides a framework for the risk-based selection of IT security measures. Rather than implementing every possible control, you select appropriate measures proportional to the risks your product faces.
This approach, available in machine-readable OSCAL format on GitHub, helps you:
- Map identified risks to appropriate security controls
- Justify security decisions with documented risk rationale
- Demonstrate proportionality to regulatory authorities
- Optimize resource allocation
Document not just what risks exist, but why certain risks are or aren't applicable to your specific product and deployment context. Notified bodies reviewing Critical products will scrutinize these justifications.
Step 3: Secure Development Lifecycle (SSDLC)
Embedding Security into Development
Security by design and development is the cornerstone of CRA compliance. This means fundamentally integrating cybersecurity into every phase of your product development process, not adding it as a final step.
Adopting Recognized Frameworks
The CRA and BSI TR-03183-1 reference established secure development frameworks. You should align your processes with recognized standards such as:
- OWASP SAMM (Software Assurance Maturity Model): Provides a framework for formulating and implementing secure software strategies
- BSI TR-03185: BSI's guideline for secure software development
- ISO 27034: Application security standard addressing security in development
You don't necessarily need to adopt these frameworks wholesale. Many OEMs successfully integrate security practices into existing development methodologies like Scrum, Agile, or SAFe. The key is demonstrating that security considerations are embedded throughout your process.
Security Throughout the Lifecycle
Requirements Phase:
- Define security requirements alongside functional requirements
- Conduct abuse case modeling to identify potential attacks
- Establish security acceptance criteria
Design Phase:
- Perform threat modeling using frameworks like STRIDE or PASTA
- Design security architectures and protocols
- Select cryptographic algorithms and key management approaches
- Document security design decisions and rationale
Development Phase:
- Follow secure coding standards (CERT, OWASP, or industry-specific)
- Implement code review processes with security focus
- Use static analysis tools to identify vulnerabilities early
- Apply compiler hardening flags and security features
Testing Phase:
- Conduct security-specific testing (penetration testing, fuzzing, vulnerability scanning)
- Use dynamic analysis and sanitizers to identify runtime issues
- Verify cryptographic implementations
- Test authentication and access control mechanisms
Release Phase:
- Generate Software Bill of Materials (more on this in Step 5)
- Conduct final vulnerability assessment
- Verify secure update mechanisms function correctly
- Prepare security documentation for customers
Establishing Security Gates
Implement security gates at key development milestones. Products cannot progress to the next phase without meeting defined security criteria. This prevents security debt from accumulating and ensures vulnerabilities are addressed early when remediation is less costly.
Step 4: Vulnerability Management
Continuous Monitoring and Rapid Response
The CRA requires active vulnerability management throughout your product's entire expected lifetime. You cannot simply sell equipment and walk away. You must maintain security support for the product's operational life, which for industrial equipment can span decades.
Building a Vulnerability Management Process
According to BSI TR-03183-1 and CRA requirements, your vulnerability management process must cover three phases:
Phase 1: Identification
Generate and maintain Software Bills of Materials (SBoMs) tracking all components in your products. SBoMs enable automated security processing and are essential for vulnerability identification.
Cross-reference your software packages against vulnerability databases like the National Vulnerability Database (NVD) to identify known vulnerabilities affecting your components.
Conduct custom vulnerability testing using:
- Compiler hardening techniques
- Fuzzing tools to discover unexpected behaviors
- Memory and thread sanitizers
- Penetration testing for deployed systems
This is where Think Ahead's continuous compliance monitoring solution becomes invaluable. Rather than manually tracking vulnerabilities across your product portfolio, our platform automatically monitors your SBoMs against emerging threats, alerting you immediately when vulnerabilities affecting your products are discovered. This ensures you never miss critical security issues that could affect your customers or your compliance status.
Phase 2: Assessment
Not every identified vulnerability requires immediate action. Evaluate exploitability within your specific product and deployment context:
- Can the vulnerability actually be exploited given your product's configuration?
- What access would an attacker need to exploit it?
- What is the potential impact if exploited?
- Are there mitigating factors in typical deployment scenarios?
Document your rationale for determinations that vulnerabilities are not exploitable in your context. Regulatory authorities may review these assessments, particularly for Important and Critical products.
Prioritize actively exploited vulnerabilities for immediate remediation. The CRA mandates specific notification timelines for actively exploited vulnerabilities, with reporting required to ENISA beginning September 11, 2026.
Phase 3: Remediation
For third-party components, coordinate with upstream package maintainers. Contribute to open-source security efforts where possible, as this benefits your entire supply chain.
For proprietary components, implement fixes internally following your secure development process.
Deploy patches via secure update mechanisms within appropriate timeframes. The CRA specifies timeframes based on vulnerability severity and exploitation status, with actively exploited vulnerabilities demanding the fastest response.
Secure Update Mechanisms
Your products must support secure, reliable updates throughout their lifecycle:
- Implement authenticated and encrypted update delivery
- Use code signing to verify update integrity
- Provide automated update notifications
- Support rollback to previous versions if updates fail
- Document update procedures for customers
For critical infrastructure and safety systems, consider staged deployment strategies allowing validation before broad rollout.
Coordinated Vulnerability Disclosure
Establish processes for receiving and responding to vulnerability reports from external researchers. BSI TR-03183-3 specifically addresses vulnerability reports and notifications.
Your coordinated disclosure program should define:
- How researchers can securely report vulnerabilities
- Expected response and resolution timeframes
- Communication protocols during investigation
- Credit and recognition policies
- Public disclosure coordination
Step 5: Documentation & SBOMs
Demonstrating Compliance Through Evidence
Comprehensive documentation is the thread connecting all CRA compliance activities. Without proper documentation, you cannot demonstrate compliance to regulatory authorities or notified bodies.
Essential Documentation Requirements
The CRA mandates specific technical documentation proving your compliance with essential requirements:
Conformity Assessment Documentation:
- How security by design was implemented for this product
- Mapping of each essential requirement to implemented security features
- Evidence of security testing and validation
- Rationale for security design decisions
Risk Assessment Documentation:
- Identified threats and vulnerabilities
- Context-specific risk analysis
- Selected security measures and justification
- Residual risk acceptance decisions
Secure Development Process Documentation:
- Description of your SSDLC processes
- Security policies and procedures
- Development standards and guidelines
- Security gate criteria and evidence of compliance
Security Architecture Documentation:
- System security architecture diagrams
- Network segmentation and isolation approaches
- Authentication and access control models
- Cryptographic implementations and key management
- Secure communication protocols
Vulnerability Management Documentation:
- Vulnerability identification processes
- Assessment criteria and methodologies
- Remediation tracking and timelines
- Update deployment procedures
Incident Response Documentation:
- Security incident detection capabilities
- Incident response procedures
- Escalation paths and notification protocols
- Forensic and audit logging capabilities
Documentation scope varies by product classification. Critical products require the most comprehensive evidence for notified body review, while Default products still need thorough documentation for potential regulatory inspection.
Software Bill of Materials (SBOM)
The SBOM is a cornerstone of CRA compliance. BSI TR-03183-2 specifically addresses SBOM requirements, defining it as a machine-readable document supporting automated security processing.
Why SBOMs Matter:
SBOMs provide transparency into your product's software composition, enabling:
- Rapid identification of products affected by newly discovered vulnerabilities
- Supply chain risk assessment
- License compliance verification
- Dependency tracking and management
- Automated security monitoring
SBOM Requirements:
Your SBOMs must include:
- Complete inventory of all software components
- Component names, versions, and suppliers
- Dependency relationships between components
- License information
- Hash values for integrity verification
Generate SBOMs in standardized formats (SPDX or CycloneDX) to ensure interoperability with security tools and customer systems.
Integrating SBOMs into Your Pipeline:
BSI TR-03183-2 emphasizes that SBOMs must be integrated into secure software development pipelines to ensure end-to-end traceability. This means:
- Automatically generating SBOMs as part of your build process
- Updating SBOMs whenever components change
- Version-controlling SBOMs alongside your product releases
- Making SBOMs available to customers and security tools
Think Ahead's platform integrates SBOM generation and continuous monitoring directly into your development ecosystem, ensuring your compliance documentation is always current and your vulnerability exposure is always visible.
Your Path to Compliance: Taking Action Today
CRA compliance is not a sprint, it's a marathon requiring systematic progress across all these areas. The key is starting now with a structured approach.
Immediate Actions
Week 1-2: Inventory
- Conduct comprehensive product portfolio review
- Classify products under CRA framework
- Create your product matrix and prioritization plan
Week 3-4: Gap Analysis
- Assess current processes against CRA and BSI TR-03183-1 requirements
- Identify critical gaps in development, vulnerability management, and documentation
- Estimate effort and resources needed to close gaps
Month 2: Risk Assessment Framework
- Establish risk assessment methodology aligned with BSI TR-03183-1
- Train development teams on risk assessment processes
- Begin risk assessments for highest-priority products
Month 3: SSDLC Enhancement
- Define security requirements for your development process
- Implement security gates and acceptance criteria
- Begin security training for development teams
Month 4-6: Vulnerability Management
- Implement SBOM generation in build pipelines
- Establish vulnerability monitoring processes
- Define remediation and update procedures
Month 6-12: Documentation & Pilots
- Create documentation templates for conformity assessment
- Run pilot projects demonstrating full compliance
- Refine processes based on lessons learned
Ongoing: Continuous Improvement
- Monitor emerging CRA guidance and standards
- Update processes as requirements evolve
- Extend compliance across entire product portfolio
Don't Navigate This Alone
The path to CRA compliance is complex, but you don't have to figure it out by yourself. Think Ahead specializes in helping equipment OEMs achieve CRA readiness through:
Strategic Guidance: We help you interpret CRA and BSI TR-03183 requirements in the context of your specific products and industry.
Process Implementation: We work with your teams to implement SSDLCs, risk assessment frameworks, and vulnerability management processes that fit your organization.
Continuous Monitoring: Our platform provides automated SBOM generation, continuous vulnerability monitoring, and compliance tracking, ensuring you maintain compliance as new threats emerge.
Documentation Support: We help you build the comprehensive documentation needed to demonstrate compliance to authorities and notified bodies.
Ready to Take the First Step?
We've created a comprehensive CRA Compliance Readiness Checklist to help you assess where you stand and identify your priority actions. This practical tool walks you through:
- Product inventory and classification
- Risk assessment readiness
- SSDLC maturity evaluation
- Vulnerability management capabilities
- Documentation completeness
Take the Free CRA Readiness Assessment →
Schedule Your Complimentary Assessment
For a deeper analysis of your CRA readiness, schedule a complimentary 30-minute consultation with our experts. We'll:
- Review your current compliance status
- Identify your highest-priority gaps
- Discuss how Think Ahead's continuous monitoring solution can streamline your compliance journey
- Answer your specific questions about CRA, BSI TR-03183, and your products
Schedule Your Free Consultation →
The December 2027 deadline is fixed, but your path to compliance can be manageable. With structured planning, the right tools, and expert guidance, CRA compliance becomes not just achievable but a competitive advantage.
The question isn't whether to comply, it's whether you'll lead or follow. Start your compliance journey today.
References:
- BSI TR-03183-1: Cyber Resilience Requirements for Manufacturers and Products - Part 1: General Requirements
- BSI TR-03183-2: Software Bill of Materials (SBOM)
- BSI TR-03183-3: Vulnerability Reports and Notifications
- EU Cyber Resilience Act (Regulation (EU) 2024/2847)